External authentication behavior
The following example illustrates how a customized eauth executable can provide external authentication of users, hosts, and daemons. In this example, the eauth executable has been customized so that corresponding instances of eauth -c and eauth -s obtain user, host, and daemon credentials from a file that serves as the external security system. The eauth executable can also be customized to obtain credentials from an operating system or from an authentication protocol such as Kerberos.
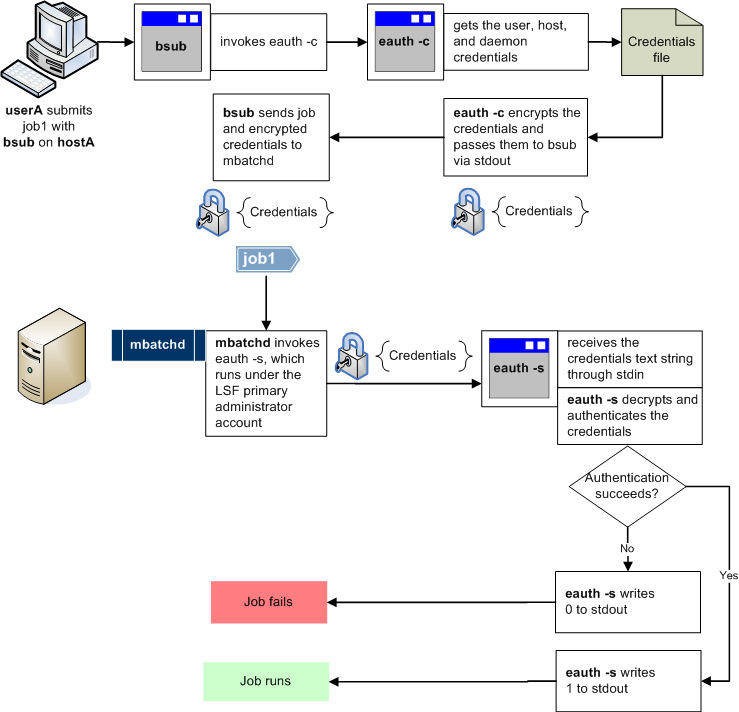
Authentication failure
When external authentication is enabled, the message
User permission denied
indicates that the eauth executable failed to authenticate the user’s credentials.
Security
External authentication—and any other LSF authentication method—depends on the security of the root account on all hosts within the cluster. Limit access to the root account to prevent unauthorized use of your cluster.